Create Windows 11 Device Collection in SCCM / Configuration Manager

In this article we will see how to create a Windows 11 Device Collection to group all Windows 11 computers in SCCM/MEMCM/Configuration Manager. A query will run periodically and will automatically include the new Windows 11 computers in the Device Collection.
You can create Windows 11 Device Collections in SCCM with WQL Queries. This way, you don’t have to add them manually. Once the Device Collection is created, you can use it to distribute applications and deploy security updates to Windows 11.
TL;DR
Windows 11 Builds Numbers (21H2, 22H1, 22H2)
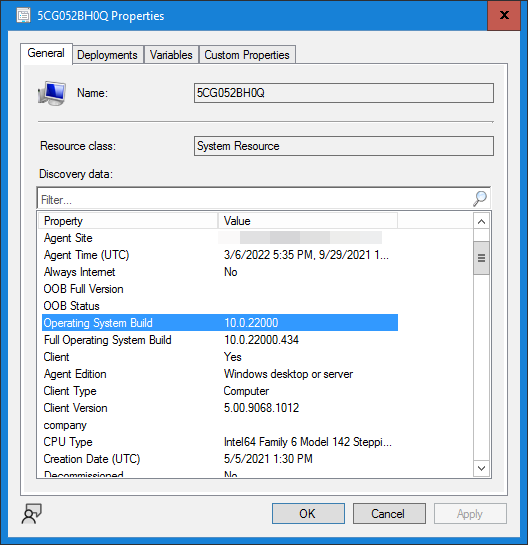
Windows 11 (like Windows 10) has various builds. Its base version is 10.0.22000, also known as Windows 11 21H2. You can view the build of a device in the SCCM console by right-clicking on a Device > Properties.
In the “General” tab we look for “Operating System Build“:
The next line you see (“Full Operating System Build“) is the full version including monthly security patches. For now it is not necessary to use this data, but it is interesting to know it in case you need to create a devices collection based on their security patches.
You can also view this data using the “Resource Explorer” by right-clicking > “Start” > “Resource Explorer“:
A new window will open with all the data of the Windows 11 device in SCCM. Go to “Hardware” > “Operating System“:
Here you have all the information you need to create a Windows 11 Device Collection in SCCM / Configuration Manager with various methods.
Queries for Windows 11 Device Collections
It is important to know all the possible ways to create a collection of Windows 11 devices in SCCM. Depending on how you want to manage Windows 11 devices, you’ll follow one way or another.
All these forms are based on the image of resource explorer in the previous section. You can copy and paste the query when creating your collection of Windows 11 devices.
Windows 11 SCCM Queries using the Operating System Name
The first method, you can use the “Name” field of “Operating System” (1 in the Resource Explorer image). It is a recommended option to include all Windows 11 regardless of its compilation (it is usually not necessary to distinguish unless a corporate application does not work in specific versions).
1 | select SMS_R_SYSTEM.ResourceID,SMS_R_SYSTEM.ResourceType,SMS_R_SYSTEM.Name,SMS_R_SYSTEM.SMSUniqueIdentifier,SMS_R_SYSTEM.ResourceDomainORWorkgroup,SMS_R_SYSTEM.Client from SMS_R_System inner join SMS_G_System_OPERATING_SYSTEM on SMS_G_System_OPERATING_SYSTEM.ResourceID = SMS_R_System.ResourceId where SMS_G_System_OPERATING_SYSTEM.Name like "%Microsoft Windows 11 Enterprise%" |
Note: In case not all your computers are Enterprise, you can change the value to “%Microsoft Windows 11%” to include any Windows 11.
Windows 11 SCCM Queries using OS Build Number
Second method, you can use the “Build Number” field of “Operating System” (2 in the Resource Explorer image). In this way you differentiate one version of Windows 11 from others. Recommended if you have applications that do not work in the latest versions of Windows 11.
1 | select SMS_R_SYSTEM.ResourceID,SMS_R_SYSTEM.ResourceType,SMS_R_SYSTEM.Name,SMS_R_SYSTEM.SMSUniqueIdentifier,SMS_R_SYSTEM.ResourceDomainORWorkgroup,SMS_R_SYSTEM.Client from SMS_R_System inner join SMS_G_System_OPERATING_SYSTEM on SMS_G_System_OPERATING_SYSTEM.ResourceId = SMS_R_System.ResourceId where SMS_G_System_OPERATING_SYSTEM.BuildNumber = "22000" |
Note: You will have to change the “22000” for the number of the Windows 11 Build that you want.
Windows 11 SCCM Queries using Operating System Caption
The third method, you can use the “Caption” field of “Operating System” (3 in the Resource Explorer image). It is the most recommended option to include all Windows 11 regardless of its compilation. Being a single text is the cleanest method.
1 | select SMS_R_SYSTEM.ResourceID,SMS_R_SYSTEM.ResourceType,SMS_R_SYSTEM.Name,SMS_R_SYSTEM.SMSUniqueIdentifier,SMS_R_SYSTEM.ResourceDomainORWorkgroup,SMS_R_SYSTEM.Client from SMS_R_System inner join SMS_G_System_OPERATING_SYSTEM on SMS_G_System_OPERATING_SYSTEM.ResourceId = SMS_R_System.ResourceId where SMS_G_System_OPERATING_SYSTEM.Caption = "Microsoft Windows 11 Enterprise" |
Note: In case of not being all Enterprise, you will have to change the “Enterprise” text for the edition you have or using “%Microsoft Windows 11%” to include all the Windows 11.
Create Windows 11 Device Collection in SCCM
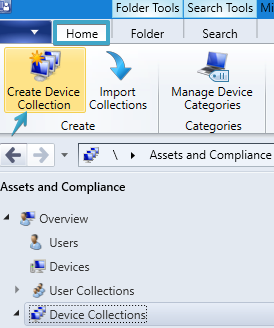
- In the SCCM console, go to “Assets and Compliance \ Overview \ Device Collections“.
- In the top menu, go to the “Home” tab and select “Create Device Collection“.
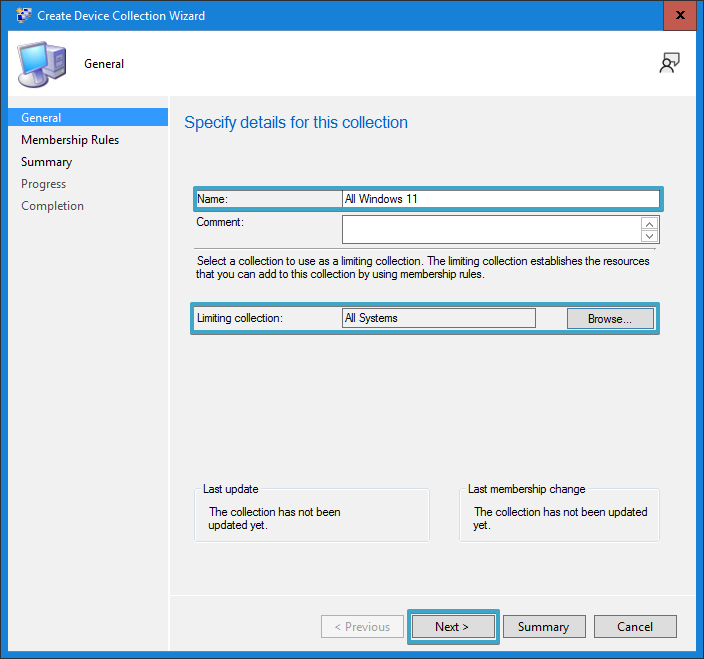
- In the “General” section, define the Name of the collection and the limit collection. Click on “Next“:
- In the “Membership Rules” section, click on “Add Rule” and “Query Rule“:
- Specify a Name for the query and click on “Edit Query Statement“:

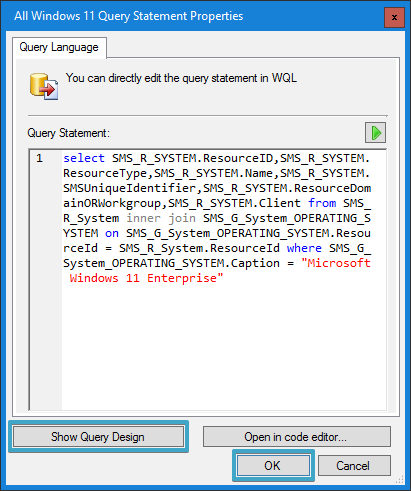
- Click on “Show Query Language” and paste the query method that you have chosen from the previous section and click on “OK“:
- Click “OK” again:
- Now activate the “Schedule” so that the collection is updated automatically. In my case I recommend that it be updated once a day. Click on “Next“:
- Click again on “Next” to confirm and after a few seconds you will see the confirmation screen:
- If you have correctly followed the instructions, you should already see our device collection of Windows 11 devices in SCCM:
With this, you can already start distributing updates on Windows 11 and publishing applications. Any questions or suggestions can be left in the comments 😁